How to Hack instagram Account with Python
How to Hack instagram Account
How to Hack instagram with Python
What is Brute-Force
Brute force is a kind of digital and cryptography attack to capture a password. Although there is no information obtained from the brute-force technique, certain passwords are tried to reach the correct password. In this method of attack, a list of many passwords, mainly simple passwords, such as 12345678 and 9787654321, which are often used by people is prepared. Then, with the help of an assistant software or manual procedure, these passwords are tried again and again to be able to login to the desired account. The software stops the process by giving a signal as soon as the correct password is found.
There are many factors that affect the chances of success in the brute-force method. How strong and comprehensive a list of passwords is in the hands of the perpetrators, the user’s difficulty in healing and even the system is open to try this method, as well as many important details of brute force attack is an important item.
Brute-force guarantees is not a useful password or password-cracking method, but also a type of attack that requires intensive time. Because the bigger the list, the more likely it will be to be an advantage, but the more passwords that will be tried. Think of it as an area where you have a street Lock key and only one lock. To unlock and unlock, you will need to try all of these countless keys.
what is an Instagram phishing attack?
friends, greetings to you all. Today, I would like to tell you about a variety of attacks that have increased so much today. The attack is called phishing attack. Or phishing with an alias. A combination of password and fishing, which means phishing capture, as can be predicted from keywords.
instagram hack no download
phishing phishing is the process of stealing your password with fake corporate identity, phone fraud, and any kind of fraud you can think of. Today, the most fake e-mail is obtained. If we set up an example scenario;

We want to know the password cheat and the person in front of us is trying to steal any account we want. For example, we’d like to steal bank a’s credit card code. First of all, we’re writing a text that can convince the other party, it could be from credit card campaigns or it could be a fake message like you need validation. We give you a link to redirect to the internet page interface where we put the script into. When the other party clicks on the link in this way, it moves to the bank’s interface and delivers the password requested by him to us with his own hands without understanding anything.
These attacks are often used to steal bank passwords with high levels of protection. In addition to this, internet banking, social media and other accounts, in short, all kinds of information containing the user name password is accessed in this way.
the attack against which Precautions can be taken ?
No bank will ask you for your private information. Keep this sentence in mind, which is now considered as the golden rule.
Access the address bar to the official website of that institution without pressing the link.
The e-mail should be terminated with the name of the institution. Example : kitchen@abankasi.com.tr
In particular, do not automate your credit card information on any site and do not leave it in registered form.
If you want to make sure that the site is authentic, click the lock icon at the top of the address bar where you want to enter the site’s name and certificate and the name and certificate of the site must match.
How To Hack Instagram Account
Every social media platform has vulnerabilities. For example, Facebook, the popular social media platform last year, has lost many users because of these vulnerabilities. Instagram, the most popular social media platform today, has been chosen by more people because of the security weaknesses of its competitors. For example, Twitter has sent an e-mail to all its users in the past months and warned them to change their account’s password due to a security breach. Why is Instagram different from them when the security of the two popular social media platforms is in the middle?
Playing Instagram account has been quite common lately. Moreover, you don’t have to be computer-savvy to play Instagram account. In fact, it is a fact that requires more intent than the ability to play Instagram account. Let’s look at the main Instagram account playback methods together.
1 – the known and most common method is the way to play the account of someone you know. To do this, you only need to know the account password or the account has a fairly simple password. This kind of situation, especially between separated couples or friends who have problems with each other, can be seen as relatively harmless.
2 – in the second way, a more complicated method is applied. If you do not have an anti-virus program on your computer and you visit many untrusted sites while surfing the internet, you are likely to infect your computer keylogger or trojan virus. This kind of viruses, all of the information you typed on your computer keyboard and sends it to the person who uses the program. Thus, not only your Instagram account, but also all your information and most private secrets can fall into the hands of malicious people. This method for the protection from an anti-virus program and periodically scan the computer provides the most appropriate solution to use.
3 – Third Way to use the internet to target foreign Instagram users. In this method, your Instagram account is played through the malicious applications that you connect to your Instagram account, such as increasing the tracker, seeing the people who are looking at the account, and seeing the hidden accounts. So if you’re using a tracker upgrade application, you should be careful. Especially considering that many people and businesses are using such applications nowadays, this can be shown as the most common Instagram account playback management.
instagram password cracker
4-Instagram is another method of account stealing, access to the location information of the account wanted to be stolen by using this information to request to renew the password is encountered. As a method of password renewing Instagram sends a link or verification code to the user’s email account. At this point, the person who wants to steal the Instagram account is confused by the social media platform, allowing code or link to be sent to another account other than the user’s e-mail account.
5 – another Instagram account as a method of playing in front of us also known as social engineering method comes out. In this method, a password is obtained by using a person’s account in the owner’s list of the account to be played. It does not require any computer knowledge because the inspiring method is applied in this method rather than technical knowledge.
How to Hack instagram Account
First install the required modules
1 | pip install argparse requests PySocks asyncio proxybroker |
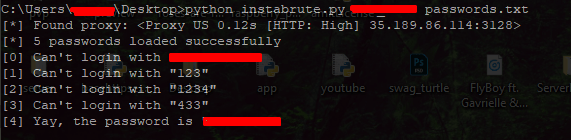
Run the script
1 2 | python instabrute.py USERNAME PASSWORD_FILE //Example: "python instabrute.py username passwords.txt" |
Modules
- argparse
- requests
- PySocks
- asyncio
- proxybroker
instagram hack project
To fully activate the Microsoft license, use KMS Activator, it is reliable and secure. https://www.kalogroup.com.au/
